xpl0it
Senior Member
- Feb 21, 2014
- 124
- 88
Brute-force attacks are fairly simple to understand, but difficult to protect against. Encryption is math, and as computers become faster at math, they become faster at trying all the solutions and seeing which one fits.
These attacks can be used against any type of encryption, with varying degrees of success. Brute-force attacks become faster and more effective with each passing day as newer, faster computer hardware is released.
Brute-Force Basics
Brute-force attacks are simple to understand. An attacker has an encrypted file — say, your LastPass or KeePass password database. They know that this file contains data they want to see, and they know that there’s an encryption key that unlocks it. To decrypt it, they can begin to try every single possible password and see if that results in a decrypted file.
They do this automatically with a computer program, so the speed at which someone can brute-force encryption increases as available computer hardware becomes faster and faster, capable of doing more calculations per second. The brute-force attack would likely start at one-digit passwords before moving to two-digit passwords and so on, trying all possible combinations until one works.
A “dictionary attack” is similar and tries words in a dictionary — or a list of common passwords — instead of all possible passwords. This can be very effective, as many people use such weak and common passwords.
Why Attackers Can’t Brute-Force Web Services
There’s a difference between online and offline brute-force attacks. For example, if an attacker wants to brute-force their way into your Gmail account, they can begin to try every single possible password — but Google will quickly cut them off. Services that provide access to such accounts will throttle access attempts and ban IP addresses that attempt to log in so many times. Thus, an attack against an online service wouldn’t work too well because very few attempts can be made before the attack would be halted.
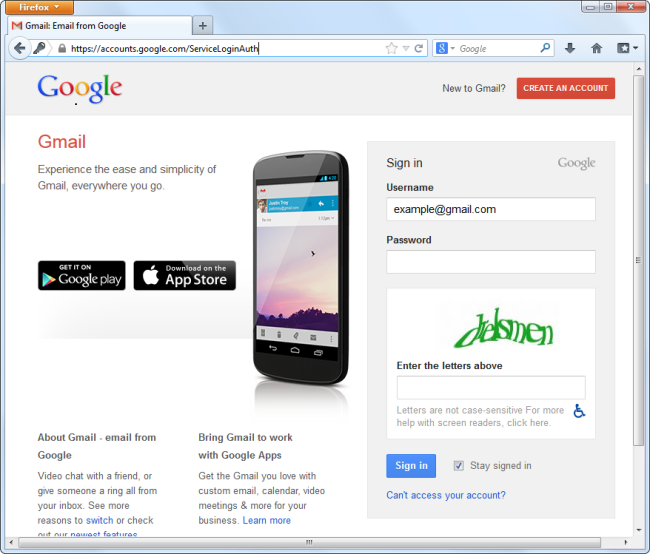
For example, after a few failed login attempts, Gmail will show you a CATPCHA image to verify you aren’t a computer automatically trying passwords. They’ll likely stop your login attempts completely if you managed to continue for long enough.

On the other hand, let’s say an attacker snagged an encrypted file from your computer or managed to compromise an online service and download such encrypted files. The attacker now has the encrypted data on their own hardware and can try as many passwords as they want at their leisure. If they have access to the encrypted data, there’s no way to prevent them from trying a large number of passwords in a short period of time. Even if you’re using strong encryption, it’s to your benefit to keep your data safe and ensure others can’t access it.
Hashing
Strong hashing algorithms can slow down brute-force attacks. Essentially, hashing algorithms perform additional mathematical work on a password before storing a value derived from the password on disk. If a slower hashing algorithm is used, it will require thousands of times as much mathematical work to try each password and dramatically slow down brute-force attacks. However, the more work required, the more work a server or other computer has to do each time as user logs in with their password. Software must balance resilience against brute-force attacks with resource usage.
Brute-Force Speed
Speed all depends on hardware. Intelligence agencies may build specialized hardware just for brute-force attacks, just as Bitcoin miners build their own specialized hardware optimized for Bitcoin mining. When it comes to consumer hardware, the most effective type of hardware for brute-force attacks is a graphics card (GPU). As it’s easy to try many different encryption keys at once, many graphics cards running in parallel are ideal.
At the end of 2012, Ars Technica reported that a 25-GPU cluster could crack every Windows password under 8 characters in less than six hours. The NTLM algorithm Microsoft used just wasn’t resilient enough. However, when NTLM was created, it would have taken much longer to try all these passwords. This wasn’t considered enough of a threat for Microsoft to make the encryption stronger.
Speed is increasing, and in a few decades we may discover that even the strongest cryptographic algorithms and encryption keys we use today can be quickly cracked by quantum computers or whatever other hardware we’re using in the future.

Protecting Your Data From Brute-Force Attacks
There’s no way to protect yourself completely. It’s impossible to say just how fast computer hardware will get and whether any of the encryption algorithms we use today have weaknesses that will be discovered and exploited in the future. However, here are the basics:
These attacks can be used against any type of encryption, with varying degrees of success. Brute-force attacks become faster and more effective with each passing day as newer, faster computer hardware is released.
Brute-Force Basics
Brute-force attacks are simple to understand. An attacker has an encrypted file — say, your LastPass or KeePass password database. They know that this file contains data they want to see, and they know that there’s an encryption key that unlocks it. To decrypt it, they can begin to try every single possible password and see if that results in a decrypted file.
They do this automatically with a computer program, so the speed at which someone can brute-force encryption increases as available computer hardware becomes faster and faster, capable of doing more calculations per second. The brute-force attack would likely start at one-digit passwords before moving to two-digit passwords and so on, trying all possible combinations until one works.
A “dictionary attack” is similar and tries words in a dictionary — or a list of common passwords — instead of all possible passwords. This can be very effective, as many people use such weak and common passwords.
Why Attackers Can’t Brute-Force Web Services
There’s a difference between online and offline brute-force attacks. For example, if an attacker wants to brute-force their way into your Gmail account, they can begin to try every single possible password — but Google will quickly cut them off. Services that provide access to such accounts will throttle access attempts and ban IP addresses that attempt to log in so many times. Thus, an attack against an online service wouldn’t work too well because very few attempts can be made before the attack would be halted.
For example, after a few failed login attempts, Gmail will show you a CATPCHA image to verify you aren’t a computer automatically trying passwords. They’ll likely stop your login attempts completely if you managed to continue for long enough.
On the other hand, let’s say an attacker snagged an encrypted file from your computer or managed to compromise an online service and download such encrypted files. The attacker now has the encrypted data on their own hardware and can try as many passwords as they want at their leisure. If they have access to the encrypted data, there’s no way to prevent them from trying a large number of passwords in a short period of time. Even if you’re using strong encryption, it’s to your benefit to keep your data safe and ensure others can’t access it.
Hashing
Strong hashing algorithms can slow down brute-force attacks. Essentially, hashing algorithms perform additional mathematical work on a password before storing a value derived from the password on disk. If a slower hashing algorithm is used, it will require thousands of times as much mathematical work to try each password and dramatically slow down brute-force attacks. However, the more work required, the more work a server or other computer has to do each time as user logs in with their password. Software must balance resilience against brute-force attacks with resource usage.
Brute-Force Speed
Speed all depends on hardware. Intelligence agencies may build specialized hardware just for brute-force attacks, just as Bitcoin miners build their own specialized hardware optimized for Bitcoin mining. When it comes to consumer hardware, the most effective type of hardware for brute-force attacks is a graphics card (GPU). As it’s easy to try many different encryption keys at once, many graphics cards running in parallel are ideal.
At the end of 2012, Ars Technica reported that a 25-GPU cluster could crack every Windows password under 8 characters in less than six hours. The NTLM algorithm Microsoft used just wasn’t resilient enough. However, when NTLM was created, it would have taken much longer to try all these passwords. This wasn’t considered enough of a threat for Microsoft to make the encryption stronger.
Speed is increasing, and in a few decades we may discover that even the strongest cryptographic algorithms and encryption keys we use today can be quickly cracked by quantum computers or whatever other hardware we’re using in the future.

Protecting Your Data From Brute-Force Attacks
There’s no way to protect yourself completely. It’s impossible to say just how fast computer hardware will get and whether any of the encryption algorithms we use today have weaknesses that will be discovered and exploited in the future. However, here are the basics:
- Keep your encrypted data safe where attackers can’t get access to it. Once they have your data copied to their hardware, they can try brute-force attacks against it at their leisure.
- If you run any service that accepts logins over the Internet, ensure that it limits login attempts and blocks people who attempt to log in with many different passwords in a short period of time. Server software is generally set to do this out of the box, as it’s a good security practice.
- Use strong encryption algorithms, such as SHA-512. Ensure you’re not using old encryption algorithms with known weaknesses that are easy to crack.
- Use long, secure passwords. All the encryption technology in the world isn’t going to help if you’re using “password” or the ever-popular “hunter2”.